RBAC Implementation
Role-Based Authorization on RASP Platform
Role-Based Access Control (RBAC) is an approach to managing user permissions by assigning roles to users and associating those roles with specific access rights to resources or actions within a system. Rather than assigning permissions to individual users, RBAC allows for efficient management by grouping permissions under roles like "Admin," "Editor," or "Viewer." This makes it much easier for administrators to manage who can view, edit, or delete information, and it helps keep systems secure. RBAC is useful for organizations because it simplifies controlling access, improves security, and makes it easier to track and enforce access rules across large systems.
The RASP platform has an inbuilt authorization service, and we will be extending these capabilities to implement Role-Based Authorization for API access and functionality control.
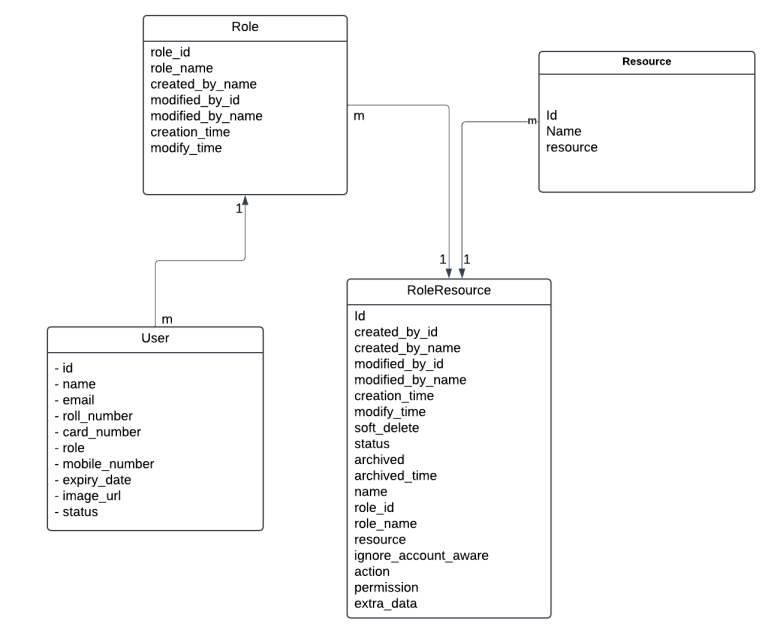
Role-to-Resource Mapping and User Interaction
The role-to-resource mapping and user permissions can be understood from the following diagram:
Changes Required
-
application.properties:- In
backend/src/main/resources/application.properties, set:rbac.enabled=true
- In
-
backend/src/main/resources/static/ui/json/user.json:- In this file, create different users (Roles) and define which resources or applications they will have access to, along with the type of access.
- Example: A Traveler can have "view" access to a flight but will not have "modify," "delete," or "add" access.
- Allowed operations for users include
add,modify,view,delete, or any custom operation.
-
backend/src/main/java/com/example/demo/controller/BaseController.java:-
This file contains the implementation logic. Here’s a sample code for role validation:
void validateRole(ServletContext ctx, String action) throws ApplicationException {
if (rbac_enabled) {
String userId = ctx.getUserId();
User user = (User) UserHelper.getInstance().getById(userId);
if (user == null) {
throw new ApplicationException(ExceptionSeverity.ERROR, "Invalid ID");
}
if (user.getRole() == null) {
throw new ApplicationException(ExceptionSeverity.ERROR, "Role id not found!!");
}
String resource = service.getResource().getMetaData().getName();
RoleResource roleResource = (RoleResource)
RoleResourceHelper.getInstance().getByExpressionFirstRecord(
Expression.and(
new Expression(RoleResource.FIELD_ROLE_ID, REL_OP.EQ, user.getRole()),
new Expression(RoleResource.FIELD_ACTION, REL_OP.EQ, action),
new Expression(RoleResource.FIELD_RESOURCE, REL_OP.EQ, resource)
)
);
if (roleResource == null) {
throw new ApplicationException(ExceptionSeverity.ERROR, "Access denied!!!");
}
}
} -
Here,
ctxstores the context, allowing access to user ID and resources.
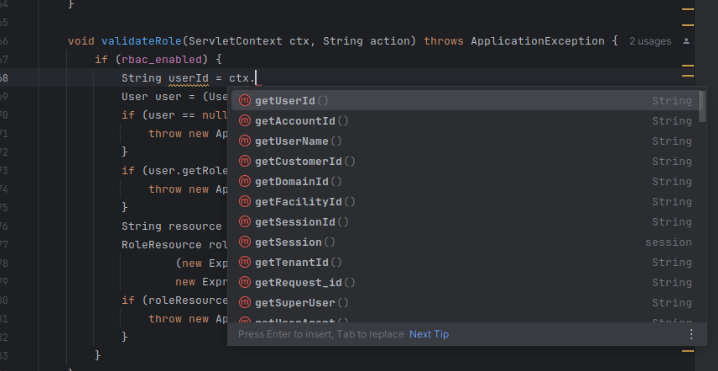
- The context will give us the logged in user whose session is currently active. From user,
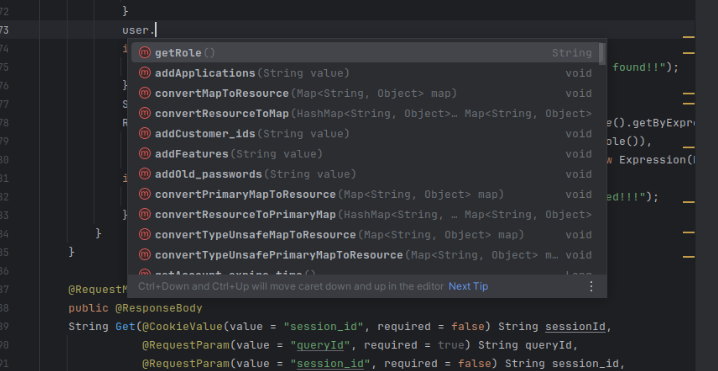
- Using the context, we can verify that only authorized users are accessing the resource.
-
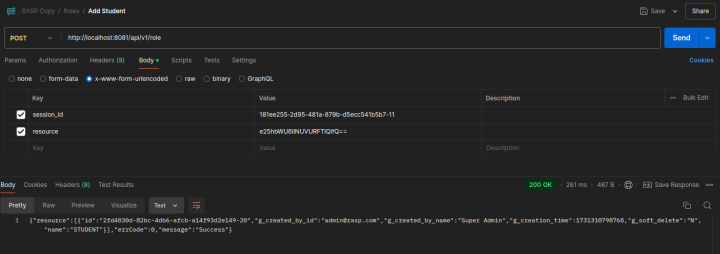
Postman API Usage
Adding a New Role
API:
POST | http://localhost:8081/api/v1/role
Request Body:
- Key:
session_id- Value: Session ID received after successful login
- Key:
resource- Value: Encoded form of the role you want to add, e.g.,
{name:"TRAVELER"}encoded in BASE64 ase25hbWU6IlNUVURFTlQifQ==
- Value: Encoded form of the role you want to add, e.g.,
Response:
200 OK
{
"resource": [
{
"id": "2fd4030d-82bc-4db6-afcb-a14f93d2e149-20",
"g_created_by_id": "[email protected]",
"g_created_by_name": "Super Admin",
"g_creation_time": 1731310798768,
"g_soft_delete": "N",
"name": "TRAVELER"
}
],
"errCode": 0,
"message": "Success"
}
Sample -
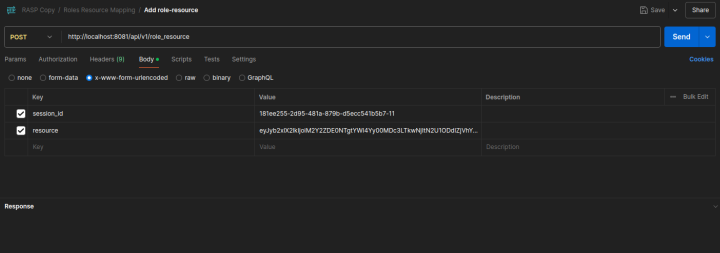
Adding Role-to-Resource Mapping
API:
POST | http://localhost:8081/api/v1/role_resource
Request Body:
- Key:
session_id- Value: Session ID received after successful login
- Key:
resource- Value: Encoded form of role ID, resource, and action
Example:
{
"role_id": "3f6d1458-ab8c-4077-9062-7e587ef5abf6-66",
"resource": "flight",
"action": ["GET_ALL"]
}
Response:
200 OK
{
"resource": [
{
"id": "f85457d9-49fb-4459-9d41-30dd8ce2964b-31",
"g_created_by_id": "[email protected]",
"g_created_by_name": "Super Admin",
"g_creation_time": 1731332313551,
"g_soft_delete": "N",
"role_id": "157fb416-397d-451b-a142-f5569ad4fbdd-29",
"role_name": "Admin",
"resource": "flight",
"action": ["GET_ALL"]
}
],
"errCode": 0,
"message": "Success"
}
Sample -